Introduction:
WiFi, a ubiquitous technology that powers our digital world, has become indispensable in everyday life. Whether at home, in the office, or on the go, WiFi networks facilitate seamless connectivity. However, researchers have uncovered a fundamental security flaw in the IEEE 802.11 WiFi protocol standard that presents a hidden danger to users. This flaw, which allows attackers to hijack network traffic, has profound security implications. Let’s dive into the details and explore how this flaw works, its impact, and what can be done to mitigate the risks.
Part 1: WiFi Frames, Encryption, and Power-Saving Mechanisms
To understand the flaw, we need to begin with the basics of WiFi frames. WiFi frames are data containers that consist of three parts: a header, a data payload, and a trailer. The header includes information such as the source and destination MAC addresses, while the data payload contains the actual data being transmitted. The trailer marks the end of the frame.
These frames are typically encrypted using one of two keys: a group-addressed encryption key shared among all devices in the WiFi network or a pairwise encryption key unique to each device. Encryption ensures the confidentiality and integrity of data exchanged between devices.
The IEEE 802.11 WiFi protocol standard also includes power-saving mechanisms. WiFi devices can enter sleep mode to conserve power. During this time, an access point buffers or queues frames destined for sleeping devices. The standard specifies that a client station (receiving device) sends a frame with a power-saving bit to the access point, causing all frames for that client station to be queued.
Part 2: The Discovery of the WiFi Protocol Flaw
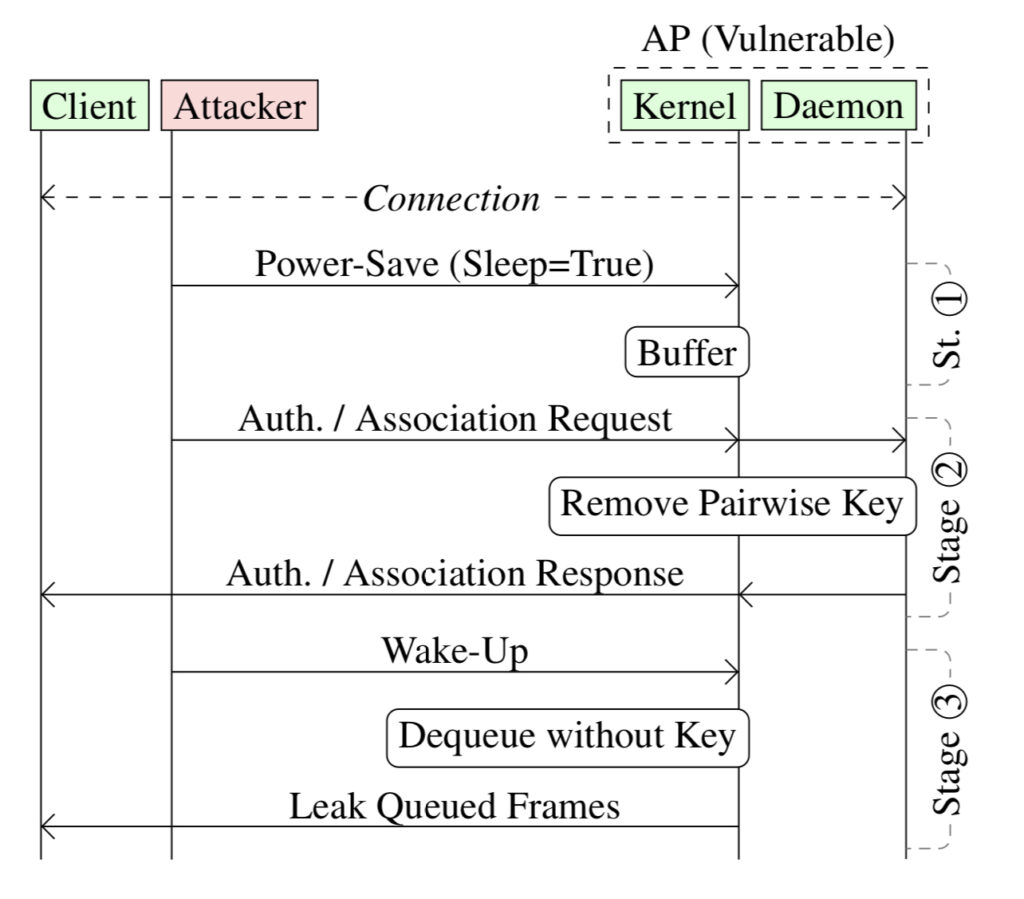
The researchers discovered that the IEEE 802.11 standard lacks explicit guidance on managing the security of queued frames and imposes no limitations on how long frames can stay in this state. This oversight leaves the queued frames inadequately protected from adversaries.
The flaw can be exploited in the following manner:
- An attacker spoofs the MAC address of a device on the network.
- The attacker sends power-saving frames to access points, forcing them to queue frames destined for the spoofed device.
- The attacker transmits a wake-up frame, prompting the access point to dequeue the buffered frames and transmit them.
- The attacker changes the security context of the frames by sending authentication and association frames to the access point. This forces the access point to transmit the frames in plaintext form or encrypt them with an attacker-provided key.
This attack can be carried out using custom tools, such as MacStealer, which can test WiFi networks for client isolation bypasses and intercept traffic at the MAC layer.
Part 3: Widespread Impact and Security Implications
The flaw affects various devices and operating systems, including Linux, FreeBSD, iOS, and Android. Attackers can hijack TCP connections, intercept client and web traffic, and even inject malicious content such as JavaScript into TCP packets. The injection of malicious content could be used to exploit vulnerabilities in a client’s browser or serve as a gateway for further attacks.
Several network device models from well-known manufacturers, including Lancom, Aruba, Cisco, Asus, and D-Link, are vulnerable to these attacks. The widespread nature of the flaw raises significant concerns about the security of WiFi networks.
Part 4: Mitigating the Risk and Recommended Practices
As of now, there are no known cases of malicious exploitation of this flaw. However, users and network administrators need to take proactive measures to mitigate the risks. These measures include:
- Implementing transport layer security (TLS) to encrypt data in transit.
- Using policy enforcement mechanisms to restrict network access and implement role-based access controls.
- Configuring network access restrictions and client isolation to prevent unauthorized devices from accessing the network and interacting with other devices.
- Regularly updating and patching network devices to address known vulnerabilities and ensure the latest security features are in place.
- Deploying intrusion detection and prevention systems (IDS/IPS) to monitor and block suspicious network activities.
- Educating users about the importance of strong, unique passwords for WiFi access and avoiding the use of default credentials provided by manufacturers.
Manufacturers and standard-setting organizations also have a crucial role to play in addressing this flaw. They are encouraged to:
- Provide explicit security guidance for managing queued frames within the IEEE 802.11 standard.
- Release firmware updates to address the vulnerability in affected network devices.
- Work on enhancing the security features of future WiFi protocol standards to prevent similar flaws from arising.
Conclusion:
The discovery of the WiFi protocol flaw serves as a stark reminder of the importance of cybersecurity in a connected world. As WiFi technology continues to evolve and become more sophisticated, so too do the threats that seek to exploit it. By staying informed and taking proactive measures, users, network administrators, and manufacturers can work together to build a secure and resilient digital landscape.
As we continue to rely on WiFi networks for communication, work, entertainment, and more, understanding the underlying vulnerabilities is paramount to ensuring our security. By shedding light on this hidden danger, we hope to empower individuals and organizations to navigate the digital world with confidence and peace of mind.
